Developing News Story: Yahoo Hacked | 7 Ways to Protect Yourself from the Biggest Breach in History!
On Thursday of last week, Yahoo Inc. (Yahoo!) confirmed that hackers had cracked Yahoo’s servers and stolen information from over 500 MILLION users.
But what if you don’t use Yahoo? Are you still impacted? Possibly, since you might have had a Yahoo account in the past that you stopped using, or you might have used one of the thousands of sites, services or products that Yahoo owns or has partnered with, including Tumblr (owned by Yahoo) and AT&T (partner to Yahoo), and created a Yahoo account without realizing it.
Irrespective, it is worth taking the 7 precautions outlined below. CNN is reporting this news as “the biggest hack and data breach in world history ever.”



Image Source: Yahoo Hacked
Yahoo Inc. announced last Thursday that the hackers were backed by a “state-sponsored foreign government” and might have stolen user account information, including user names, email addresses, phone numbers, birthdays, hashed passwords, and answers to some security questions and answers.
You can read Yahoo Inc.’s entire press announcement right here: http://www.businesswire.com/news/home/20160922006198/en/
The hackers initially gained entry two years ago, but Yahoo did not realize that it had been breached, nor did it understand the scale of the breach until now, when it confirmed the attack. It was not immediately clear when exactly Yahoo learned that it had been hacked and why it took two years for this to come to light.
“It’s not yet clear what the motives were but it’s not to simply leak (or sell) the credentials and call it a day,” said Michael Borohovski, CEO of Tinfoil Security, during a CNNMoney interview. Security experts say the information obtained could be used for everything from blackmailing and spamming users to discovering their passwords on other services.
If you have ever had a Yahoo! account or if you still do, chances are that you are now a victim of the world’s largest hack attack.
In general, here are 7 tips on how you can minimize the possibility of falling victim to a hack attack or data breach.
7 Ways to Minimize Your Risk
Cybersecurity specialists recommend using a different password for every online account you have.
But we all know that is NOT a realistic recommendation.
How can anyone store that many passwords in his or her head? Or perhaps you store all of them on an Excel document or other document on your computer, but what if your computer gets hacked?
In general, “hackers know that consumers use the same passwords across websites and applications, which is why hacked leaked password credentials are so useful for perpetuating fraud,” stated Brett McDowell, executive director of the FIDO Alliance, an organization that vets the security of password alternatives.
So, since it is not a realistic expectation to use a single password for EVERY account, the next best recommendation would be that people not use the same password for multiple important accounts.
It’s recommended that you remember a few master passwords, store other passwords in a plain text file – encrypting this file with 7-Zip, GPG or disk encryption software such as BitLocker – or manage your passwords with a password management software.
You can also encrypt and back up your passwords to different locations. This way, if you lose access to your computer or account, you can retrieve your passwords very quickly.
(2) Always Use Powerful Passwords with Ambiguous Characters
Make your password harder to hack.
Difficult-to-hack passwords include uppercase and lowercase letters, numbers, and special symbols. Strong passwords should be at least 16 characters in length.
Use sites, like Passwords Generator, to create extremely powerful and secure passwords: http://passwordsgenerator.net/
Passwords Generator is a free site and has a very simple-to-use password generation tool (see below screenshots).
You can specify the password length, and check some boxes to specify that you want to include symbols, numbers, and lower and uppercase characters as well as exclude similar characters. You then click on “Generate secure password” and are done!


Source: Passwords Generator

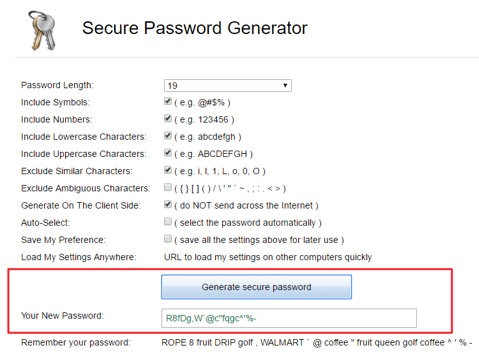
 Source: Passwords Generator
Source: Passwords Generator
All-in-One Change Management Tools
Top Rated Toolkit for Change Managers.
Get Your Change Management Tool Today...
(3) Turn on Two-Factor Authentication
On its own, a password isn’t a strong line of defense. Adding a second type of authentication, like a one-time unique code sent via a text message or generated by an app, can greatly secure your online accounts.
Two-factor authentication (also known as 2FA) is a method of confirming a user’s claimed identity by utilizing a combination of two different components.
(4) Never Click on an Email Link That Is Connected to Important Websites
Access important websites (e.g. PayPal, your bank account or other financial accounts) directly from your bookmarks, or type in the address directly onto your browser.
Never click on any links on any emails. Phishing emails often appear to be from legitimate companies that you know, but they are not and include links that aim to steal your password.
Do not reset your passwords by clicking links on an email, unless you are the one that requested to have your password reset.
(5) Change Passwords Often & Encrypt Them
The general recommendation is that you should change your passwords every 10 weeks. Encrypt and back up your passwords to different locations; then, if you lost access to your computer or account, you can retrieve your passwords quickly.
(6) When Traveling
Do not log in to important accounts when using the computers of others or when using your laptop to connect via a public Wi-Fi hotspot (airport or hotel)
(7) Use Different Emails
Use at least two different email addresses: use one to receive emails from important sites and apps, such as from your bank, and use a different one to receive emails from unimportant sites and apps.
This story was originally published at 5:22 PM CST on 9/25.
Updates: 6:20 PM (9/25/2016), 11:48 AM (9/26/2016), 1:24 PM (9/26/2016)
AdvisoryHQ (AHQ) Disclaimer:
Reasonable efforts have been made by AdvisoryHQ to present accurate information, however all info is presented without warranty. Review AdvisoryHQ’s Terms for details. Also review each firm’s site for the most updated data, rates and info.
Note: Firms and products, including the one(s) reviewed above, may be AdvisoryHQ's affiliates. Click to view AdvisoryHQ's advertiser disclosures.